CHECKPOINT FIREWALL TRAINING INTRODUCTION:
Checkpoint Firewall is an international provider of software and combined hardware and software products for IT Security, including network security, endpoint security, data security and security management. A Network Administrator needs to be constant aware of the threats to the organization’s network, data and protect these by proactive deployment of firewalls and instruction prevention systems.
Checkpoint Firewall Training designed with Checkpoint Firewall architecture and checkpoint terminology. IdesTrainings gives high quality training and we also provide cost effective learning. Register yourself in the website to know more about this course, to gear you in and around the Checkpoint Firewall and its specialization.
Checkpoint Firewall Training Prerequisites:
- Attendees should have knowledge on troubling, basic security concepts.
CheckPoint Firewall Corporate Training Outline:
- Mode of training : Checkpoint firewall online training / Checkpoint firewall Corporate Training
Duration of Course : 30 Hours (It can also be optimized as per required period)
Materials : Yes, we are providing materials for best Checkpoint firewall online training.
Course Fee : please register in our website, so that one of our agents will assist you.
Trainer Experience : 10+ years.
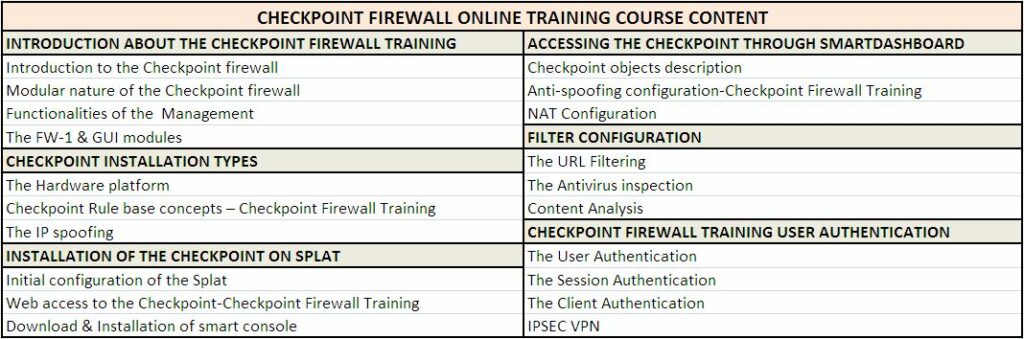
CHECKPOINT FIREWALL ONLINE TRAINING COURSE CONTENT
Our aspiration is to create a place where professionals can gain knowledge and can get ideas to build a better career and better learning experiences all time. The most active online corporate trainings for learning folks! It will help you in gaining knowledge in all IT fields, Idestrainings is an online training center with experienced trainers around the world. Register to get regular updates on online trainings and our experts will guide you through the entire training process for perfect solutions.
Purpose of Checkpoint firewall training:
The checkpoint firewall has few ideas basics of checkpoint firewall architecture, there are diverse operating systems and models for the checkpoint firewall. And there are few GUI compounds. You will learn about the security and NAT regulations and also about troubleshooting problems.
Architecture of Checkpoint Firewall:
- In the checkpoint firewall architecture there is three tier proficiency, they are GUI, MM and FW.
- The GUI is the Smart Console GUI application in the SmartDashboard that is to create and manage the security policies by the system administrator.
- The MM is the security management server that will manage the security procedure that will organize the databases stored in the security management.
- The FW will act as the security enforcement peak and security gateway will put into effect in the organization.
- There are few technologies in the organizations like distributed and standalone deployment, gateway and security policies and the Security Management server Smart Console Smart Dashboard are created by the administration for incoming and outgoing communications.
Overview of Checkpoint Firewall Features:
- The accomplishment of the Internet makes longer deep inside enterprise network, haze the line between concealed & public networks. Internet expertise is the lashing universal business rebellion
- You can see how you can make use of critical communications travelling more than assorted association, security deployments have to to defend project networks beside interruption and make certain the retreat and reliability of the communications in this Checkpoint firewall training.
- This will complete enterprise security explanation so as to defend networks, applications, and users each and every elements of the project network. The end to end network security delivered for the Secure Virtual Network architecture uniquely that will defend the business related Internet, intranet and extranet interchange.
- There are few important factors in the checkpoint firewall those are listed like it has some specialized vendors that only create the firewalls. The firewall has the connection based granularity and it has many platforms that will manage the servers. It has hardware platforms and the operating systems also. Based on the SmartConsole it has the enhanced management tools. This checkpoint firewall has the GUI which is very easy to troubleshoot and that is simpler. This is not related to the java companionable.
You can come across the Checkpoint firewall training in Idestrainings; we will provide online education with the proficient supervision, in here you can come across vibrant itinerary that can be trained anytime and at anyplace.
About Cluster in the checkpoint training:
In this checkpoint you can learn about the ClusterXL and the modes of the clusterXL which are related to the checkpoint. The synchronization of clusterXL and cluster control protocol will be explained. Basically the user starts using the internet then the traffic will be forwarded to the firewall and then to the internet. In case the firewall got troubled then the user will not get the information.
- When users will drop any question in the query box then the request will go to the firewalls then to the internet, this firewall controls the traffic among the internal and the external networks of the network policy. The security will be checked by the Security Gateway or Security Management server, and there will be the checkpoint software blades that will check that these security features are working correctly or not.
- There are some parts in the checkpoint software blade those are, connectivity of the mobile devices and the VPN, identity and awareness of the computer, filtering through the internet, application control and the data loss prevention.
- The architecture of the Secure Virtual Network exclusively distributes the back-to-back network security that facilitate project of the business to protect from decisive internal and external traffic.
- Security has all time been one of the most important aspects of network. As security deployments become more complicated with addition of mobile connectivity & the Web services, enterprises are looking for comprehensive answers. With the joint solution between security leader
Checkpoint needs clustering because, to get to the internet in between you will have the firewall, and then it will send to the server which you are accessing. If suppose the firewall will be crashed then the information will not reach you from respected server, so in this case the clustering will be the solution that will take care of the redundancy. Redundancy means, if suppose the firewall is failed then it will go to the backup firewall then the traffic will go to the internet. There is the fault tolerance that means, if you have many systems then each system will have the separate firewalls
Conclusion:
IdesTrainings put forward the best checkpoint firewall training for professionals and as well as the students, and we offer them an outstanding insight in excess of this checkpoint firewall online training. The entire classes will be like 100% interactive platform for the participants. As well as, the tutorials are made by subject matter experts with ample hands-on awareness on their real project.

