
CEH TRAINING COURSE INTRODUCTION:
CEH Training is the most comprehensive course for network security professionals, Certified Ethical Hacker Credentials, IT security specialists like an integrator tester or ethical hacker. Training for CEH is to protect networks against numerous vulnerabilities that weaken a person’s abilities. CEH-Certified Professional Tester, Network Security Expert, Moral Hacker, Security Advisor, Site Administrator and General Job Titles for Auditors.
IdesTrainings offers CEH Training with in-depth knowledge and practical experience with the current essentials security systems. Trainees begin by understanding how perimeter defense works and then scans and attack their own networks. Learn how to manage and keep your system safe. To more information about CEH Training feel free to contact us on the Idestrainings help desk.
Prerequisites:
- Attendance Linux and strong Microsoft Windows skills should have knowledge of work.
- You must have a working knowledge of TCP / IP.
- Background in security or information systems.
- Additional knowledge of the network technologies.
CEH Training Course Outline:
- Course Name: CEH Training
- Mode of training: Online classes and Corporate Training
- Duration of course: 30 hrs
- Do you provide materials: Yes, If you register with IdesTrainings, the materials will be provided.
- Trainer experience: 15 years+
- Batch Type: Regular, weekends and fast track
CEH ONLINE TRAINING COURSE MODULES
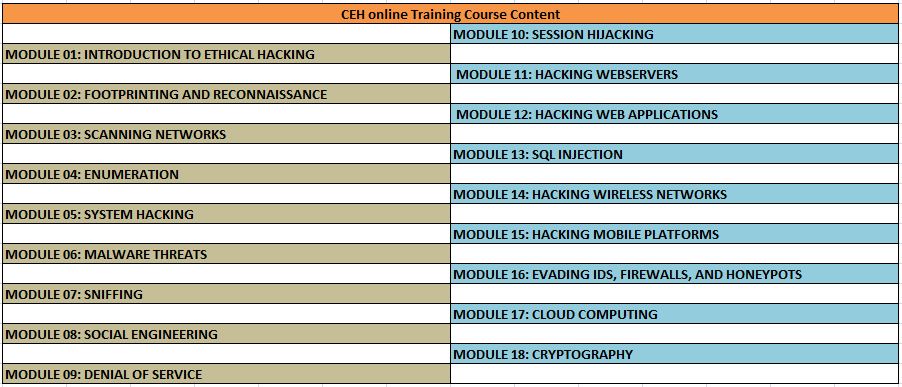
CERTIFIED ETHICAL HACKER ONLINE TRAINING COURSE CONTENT
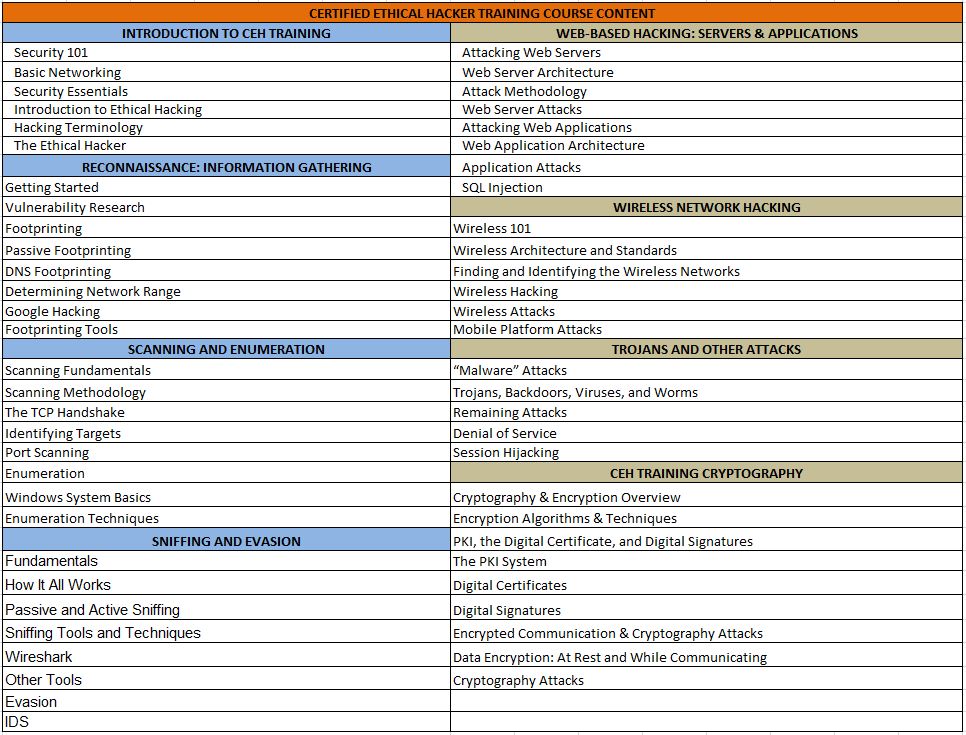
CEH Training Overview:
The Certified Ethical Hacker Training Program is the most prominent information security training program with the information security professional wants to be ever. As a master of hacking technologies, you need to become a hacker, but one with a moral white hat. The CEH accredited course provides advanced hacking tools and techniques to enter companies that use hackers and information security professionals.
The CEH online training course brings you to hacker mode and can save future IT attacks. The safety mindset in any organization is not limited to some sellers or technicians. This moral hacking course puts you in the environment with a systematic process. In this course, you teach moral hacking and various ways to achieve your target system and make a breakthrough during the predefined definition. These five phases involve spying, access, emulation, accessing and covering your tracks. These five stages of hawking tools and techniques have proven briefly to identify you when using an attack against your goals.
Hey
Are you looking for an ethical hacking course? Do you think about a career in ethical hacking?
So yes, this course is for you!
What is CEH?
This Certified Ethical Hacking serves as the foundation stone for your career, providing an entrance test and security for networks and websites. With all the latest tools and real-time hacking technologies, this ethical hacking course offers you a practical approach and simulation environment to test attacks and assess the dangers. As the EC Training Authority Training Center, you have the most appropriate guarantee.
What is the purpose of learning CEH?
- Establish and maintain minimum standards for confidence in professional information security professionals in moral hacking activities.
- Give people who meet or exceed the minimum standards of trusted individuals.
- Strengthen moral hacking as a unique and self-contained career.
What you will learn in this course?
- Usage of spreading methods to assess computer security
- Prepare for EC-Council Certified Ethical Hacker Exam 312-50
- To obtain practical experience with fishing, exploitation, and sniffing strategies
- Scan, test and hack security systems and applications
- IS Hacking Legal or Not?
- Corporate World why Requires Information security?
- Ethical hacking and different types of hackers
- Network basics & how devices interact inside a network
- OSI Model and TCP/IP Protocol Suite
- Linux Hacking and Vulnerabilities
- Gather information about website, domain, people, such as emails, social media accounts, emails and friends
Who is the right person to learn this course?
- Certified Ethical Hacker or CEH V9 is the most valuable certification for those interested in pursuing a career in cybersecurity and outreach testing.
- Of course, it will be in-depth knowledge of network, web application, mobile, WiFi hacking, and counter makers and other domains that offer endless job opportunities.
Objectives for CEH Training:
- Penetrate into network systems using various to test the strength of a network.
- In this Certified Ethical Hacker training, you will learn how to test, hack and secure networks and systems in this CEH training program.
- Get in-depth theoretical knowledge of certified ethical hacking training and rich practical experience in hacking test networks.
- Learn perimeter defenses to scan & attack own networks.
- Learn various techniques such as Intrusion Detection, Social Engineering, Policy Creation, Buffer Overflows, DDoS Attacks, Virtual creation, etc.
- Understand a variety of hacking attacks and threats to the computing technology in this ethical hacking course.
- Specify various remedies to encounter cloud computing attacks.
- Understanding in-depth pen testing techniques to identify threats in cloud systems.

- Explore how to hack using mobile phones.
- In this CEH training, you will learn about the latest virus, Trojan and back-doors.
- Understand information security controls, laws, and standards in this hacking training.
Types of hackers in the cyber world:
White Hat Hacker:
This is used to describe an Ethical Hacker. The term comes
after the hackers contacted network security and systems. White hat hacking software for security and breach includes testing systems. Often network operators also make maliciousness for hacking on their
own systems. As a rule, a white hat hacker cannot enter a system, he has no power to own or enter. They follow hacking ethics later.
Black Hat Hacker:
It is used to describe a cracker or a malicious hacker. In particular, it does not apply to all computer criminals, but there are only network intruders and other activities contrary to hacker morality under this category.
Grey Hat Hacker
It can swing on the track when someone violates the system. Ether informs that this breach is a hike or shares information with people. It often violates a gray hat hacker system because he can do it. They believe that this is good for intruders. The line between the black hat and gray hat after the infiltration system is unclear, the same. However, what is the result of the end
CEH v10 Training:
The CEH (V10) modules from CEH (v9) have been updated on some important aspects of Cybersecurity Vulnerability Analysis, IOT equipment, attack vectors, and malware analysis. Prevalence testing tools are also preferred. Throughout the route, you must use the same methods as “bad guys”, including the engineering of social engineering, and even physical safety evaluation. Enhancement of the methods that hackers actually use to infiltrate networks and devices; That is, writing viruses, and reverse engineering, etc. You will learn networks, communication infrastructure, and end systems to identify safety loopholes and study vulnerability analysis.
The updated CEH v10 includes the following changes made by the EC-Council:
- Upgraded Vulnerability Assessment material
- CEH practical exam
- A module on the Internet of Things Security
- Increased target on AI, Machine Learning and cloud attack vectors.
EC-Council Training:
EC-Council Training sets the standards for cybersecurity once more with its new release of CEH V10. This authorized a new course provides you with the advanced hacking tools and techniques utilized by the knowledge security professionals. Earning the CEH v10 certification in Bharat can modify you to own a hacker mentality and causes you to defend the longer term. The course is ANSI 17024 compliant and teaches the 5 phases of moral hacking.
The 5 phases embrace intelligence, Gaining Access, Enumeration, Maintaining Access, and Covering your Tracks.
Encryption Algorithms (CEH Training):
- Encryption algorithms can be broken into asymmetric, and hashing algorithms. Each of the CEH training has different methods, strengths, weaknesses, and uses.
- Algorithms can also be broken into streaming or block ciphers and use different applications.
- Some algorithms are considered weak or broken and are generally not used. These algorithms and their implementation techniques are the hacker’s goal.
- Encryption forces are based on two main factors: key strength and algorithm strength.
- The key strength is related to the length and complexity of the key.
- The strength of the algorithm is related to the mathematical complexity of the algorithm.
- The weaknesses and strengths of different algorithms are also implemented.
- The algorithms can be split in equal, unequal, and hashing, and may include block or streaming algorithms.
Public Key Cryptography:
- Public Key cryptography uses uneven secret writing ways and algorithms and needs a handful of connected
- In CEH training the Public Key Cryptography used to encrypt, digitally sign, and verify data sent over networks or the internet – users public and private keys to encrypt and digitally sign messages.
- Can also be used to securely send symmetric or session keys – hybrid solutions.
- Public Key: Encryption key that is kept secure and never transmitted.
- Public key encrypts a message, but only private can decrypt anyone can encrypt a message to you, but only you can decrypt it.
- To digitally sign the message, the reverse happens:
- Private key encrypts a hash or digest of the message and the public key decrypts.
- Since only you possess the private key, it is considered “signed” by you and authentic.
- Public keys have to be reliably distributed prove they are tied to a valid private key.
- Distributed certification is issued from a trusted source that verifies the identity of the user and its connection to their private key.
The scope of Ethical Hacking:
Wipro Infosys and IDM in India are interested in Ethical hackers employees in India.
According to Nazi India, more wages than other areas, the ability to find a new system of inner work for a system and finding a new weakness in any safe system compared to 77,000 Ethical hackers with 15,000 hackers you can easily find the building of the career and take it to the next highest level At least 2.5 lakhs per annum Sala of up to Rs 4.5 lakh that can be quantified as the experience of being in its own security system, ethical hackers assistant or work. However, those who have more than 5 years or more years of work experience courses from 10 lakh to 12 lakh per year to become an Ethical Hacker. Many organizations in India offer certificates and diploma courses in Ethical hacking and provide relevant international security certificates such as Hedge and CHF that provide ECC CCNA security and a CNP from the AC Council Offer, Intel Information System Security for Cyber, Forensics, Information Security.
Conclusion:
Certified ethical hackers use the knowledge and tools of malicious attackers to uncover the dangers of the company’s computer systems. After assessing the safety of the target system, CEH enforces the prescribed resistance, correction and protection measures to protect the system before a real violation occurs. CEH certification is vendor-neutral, so certified Ethical hackers protect a wider range of systems, irrespective of this.
IdesTrainings is a leading online training firm and it is also providing Certified Ethical Hacker Training. We are providing online training with the most experienced industry experts and they have complete knowledge of all aspects of CEH Training. In this training, you will understand the complete Knowledge and updated version and with many new features. For more details and contact information go through our official website IdesTrainings.com thank you.

