
Introduction to Centrify Training:
Centrify offers digital transformation, delivers unified identity management that gives you one single integrated architecture to manage all user identities and privileges across multiple systems for on premises and cloud environments. Centrify allows the organizations to leverage your existing identity infrastructure and processes to manage centrally, manage authentication access control, privileges single sign in security policies, activity auditing across your organization and end user benefit by having to remember only one password credentials to all business applications whether using PC, MAC or mobile devices. Ides trainings has the industry’s best expert trainers who provide Centrify training. At ides trainings we also provide Online, Corporate, Classroom trainings and provide virtual job support as well. Learn the best Centrify training from our real time trainers.
Prerequisites for Centrify training:
Basic understanding of Identity Access Management (IAM), windows/Active Directory and UNIX operating system commands.
Centrify Training Online Course Outline:
Program Name: Centrify Training.
Duration of course:30Hours (it can be optimized as per required period).
Mode of Training: We provide Online, Corporate and Classroom training. We provide Virtual Job Support as well.
Timings: According to once feasibility.
Batch type: Regular, weekends and fast track.
Materials: Yes, if you register with Ides Trainings, Centrify training materials will be provided.
Basic Requirements: Good internet speed, Headset.
Trainer Experience: 10+ years.
Course Fee: Please register on our website, so that one of our coordinators will contact you.
Centrify Training Course Content:
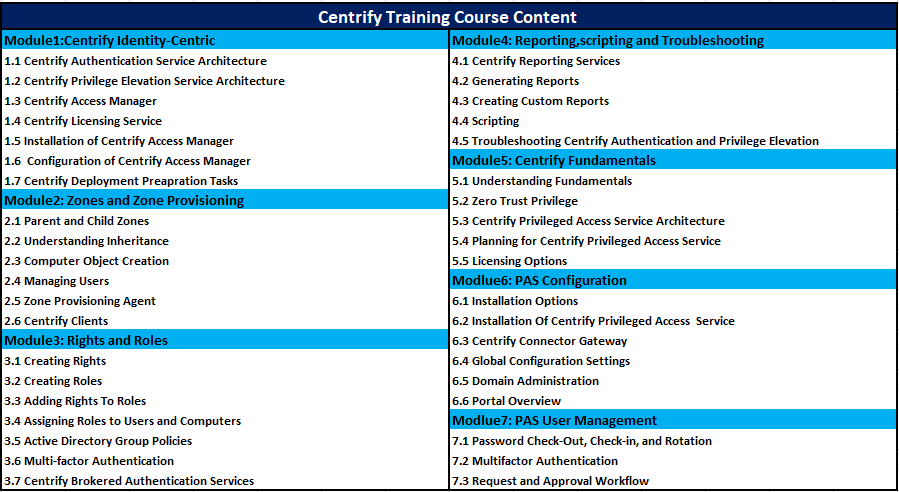
Overview of Centrify Training:
Centrify is an identity management software and cloud-based identity-as-a-service (IDaas) provider that allows programs to manage multiple identities across computer networks and cloud computing environments using Microsoft Active Directory as well as supports cloud-based directories.
Privileged Access Management:The primary goal is to have secure access to privileged accounts. For access request we basically had two factors one is a user requesting access the other is an approver who will grant or deny the request when requester makes a request either to check out a password in an emergency break glass scenario or if they want to remotely log in to a managed infrastructure. Resource workflow roots the requests to one or more approvers, if the approver denies the requests a notification is returned to the user and nothing else happens, if granted the request may not check out the password or initiate a login session to the target server. Access is granted either permanently or for a limited period of time for password check out. The Centrify shared password management service automatically rotates the password when the period is up or when the user explicitly checks the password back in. The applications of Privileged Access Management are single sign-on, adaptive MFA for App access, workflow and life cycle management, mobility management and API gateway. Another primary goal is that providing and auditing of the usage of highly privileged accounts.
MFA: Multifactor authentication(MFA):
MFA can be applied at different levels, it can be applied globally, at an individual resource level and during login process to gain access to the identity platform. Multifactor authentication is used to validate the user’s identity. It is important that you recognize how you want to set up multi factor authentication at any level within the environment. It will be promoted for our MFA challenge which is creating a security question. In multifactor authentication we will be setting authentication profiles and also policies. When we are testing the multifactor authentication with an account that has no privilege.
What are Identity Access Management and PAM tools?
It is used for ensuring the right people or machines are properly identified and given access to specific resources for a given length of time, according to the enterprises policies. But mostly IAM prefers managing Human user’s identity. Identity Access Management consist of IAM tools, the coverage gaps left by IAM tools which cybercriminal could problematic if they aren’t used in conjunction with PAM solutions. IAM is used for every user account in the organization and whereas PAM is used for securing access to key business and technical system accounts.
Capabilities of Centrify identity centric privileged access management services:
Secure remote access: This service has a number of value propositions including improving security and reducing risk. In particular, the risks associated with shared privileged accounts such as root account on Linux/Unix and the local administrator account on windows. In addition, we may have network devices such as cisco rooters that also have shared administrative accounts. Centrify takes over management of the account passwords, so the password isn’t revealed to the user. Centrify privileged access service logs them in automatically and after each session it automatically rotates the passwords to prevent it being reused, by this we improve security and remove some of the risks inherent with sharing a privileged administrative account amongst multiple people.
Identity-centric PAM for Cloud and DevSecOps:
DevOps is basically an approach or strategy build for developing the software and it is not a tool or a technology or a framework. There are a lot of conflicts between the two teams for example through software works in the developer’s laptop but it does not work in the test or the production environment. PAM solutions help assure DevOps security in many ways PAM solutions can meet the typical devOps security challenges by establishing best practices in protecting privileged access.
- Manage admin consoles
- Secure how tools talk to each other
- Eliminate the need for Hard-code or credentials in the code.
Some of the key use cases for privileged access management when we think about devops are:
- IaaS & DevOps Management Consoles
- IaaS & DevOps programmatic Access
- DevOps CI/CF Pipeline
- Cloud Infrastructure & workload security
- Elastic App configuration (secrets)
- App-to-app Authentication (AAPM, Fed Auth)
Centrify components for windows:
On windows, Centrify agent will be able to manage consoles and services to simplify the management , integration of Linux and UNIX computer and users into Active Directory.
The key components for windows that you use in deployment are:
Centrify Access Manager console
- Centrify Zone Provisioning Agent Configuration panel and windows service
There are several additional windows components available for you to use, depending on the version of Centrify software you install and the requirements of your environment. The extensions for working with NIS maps and active directory group policies, also components to support a multi-tier architecture for auditing activity uses sessions are offered by Centrify. The Centrify Network Information service to support agentless authentication service.
How PAM applications work with Centrify?
Privileged Access Management (PAM) focuses on human and non-human accounts that need access to Privileged or more sensitive information, primarily by IT administrative staff. Pluggable Authentication Modules (PAM) are a common mechanism for configuring Authentication and Authorization used by many UNIX programs and applications. If a program or applications uses PAM for Authentication and Authorization, the rules for Authenticating the users are configured in either the PAM configuration file, /etc/pam.conf or in application-specific files in the /etc/pam.d directory.
By working with adclient the pam centrifydc module is being configured to work with each other and provides the services like expiration of password checking, users and groups filtering, and creating the local home directory and default user profile files for new users. The service provided through the pam centrifyd module can be customized locally on a computer, modified through Active Directory group policy, or configured through a combination of local and Active Directory settings.
How the Centrify Agent manages Kerberos files?
Kerberos Is a network authentication protocol for client/sever applications that uses encrypted tickets passed through a central key Distribution Center to verify the identity of a user service requesting access. Because Kerberos is an industry standard and a secure network authentication mechanism, you may already have UNIX programs and services that are configured to use it. For allowance of existing kerberized applications which have to work with the Active Directory without manual configuration, the adclient process automatically creates and maintains the Kerberos configuration file ,krb5.conf,and thekrb5.keytab service ticket file to point Kerberos-enabled services and applications to the key Distribution Center (KDC) in Active Directory when you join a domain.
Centrify solutions for AWS:
Amazon web service has become one of the most popular options for extending data center infrastructure to the cloud to take advantage of cloud economy. Operating cloud and hybrid cloud environments require a focused approach to PAM. Centrify PAM delivers a solution for AWS which implements and extends identity management with best practices by access securing, controlling privilege and auditing administrative activity across hybrid environments. Centrify value suit and cloud suit brings your AWS environments under centralized management. The built-in root account password is vaulted, rotated, and access to it strictly controlled.
Who can join this course?
Anyone who has the knowledge in System administration, System Engineering, Implementation consultants, Solution consultants.
Conclusion for Centrify Training:
By the end of this Centrify training course you will have hands-on experience of installing the Centrify privileged access service into an Active directory. With IDESTRAININGS you will be learning all the basic as well as the advance concepts of Centrify in and out. IEDSTRAININGS just don’t teach you the technology rather make you to understand with real-time illustrations, the sessions we conduct are informative and interactive. IDESTRAININGS provides the best Centrify Training by corporate trainers and we also provide classroom, Online training at client premises Noida, Bangalore, Gurgaon, Hyderabad, Mumbai, Delhi and Pune.

