
CyberArk Training Introduction:
The CyberArk is the privileged management security solutions. It is the software technology which maintains and monitors the organizations on premises or in the cloud. This CyberArk privileged identity management is identify the threats like external hackers who are hacking the information from the organization database. CyberArk Training privileged account security solution is widely used by more number of sectors like in manufacturing department, insurance department, healthcare departments. IdesTrainings provide Best CyberArk Online Training by real time experienced Trainers with good material and videos. The training is available for individual and corporate batches. To know more about this online training course contact reach at help desk of IdesTrainings. Enroll now for the best CyberArk online training.
CyberArk Online Training Outline Details:
- Mode of Training: We provide online mode of training and also corporate, job support.
- Duration of Program: 30 Hours (Can be customized as per requirement).
- Materials: Yes, we are providing materials for CyberArk online training.
- Course Fee: Please register in website, so that one of our agent will assist you.
- Trainer Experience: 13+ years.
Prerequisites for CyberArk Training:
- These assist you to understand the concepts better in CyberArk training,
- Cloud Access SIEM,
- McAfee SIEM,
- Red Hat Linux,
- Privilege Account Security,
PIM, Red Hat / Linux and IT security.
Online training is now days very much convenient to the audience who are new to e-learning. Who are new to e-learning can understand how an online training sessions can be conducted. For full details about the course please register yourself in the website.
CyberArk Online Training Course Content:
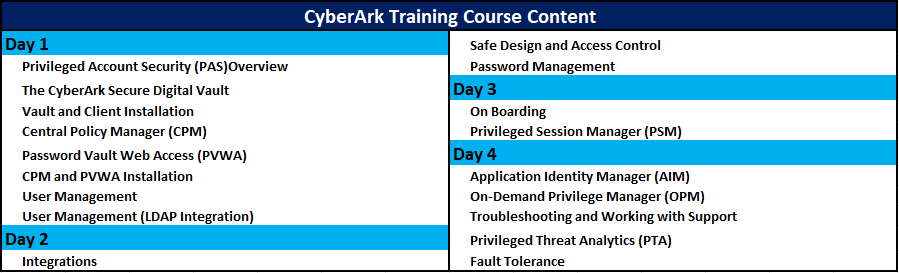
Let’s jump right in Overview of CyberArk Training:
CyberArk privileged account security (PAM) is an industry legend in file transfer solution with security. This is helped to many global enterprise users and also most of the other users. This is widely used by the consultant companies, financial services like banking insurance departments.
CyberArk is very valuable tool to provide security to the organization information.
This CyberArk Training privileged Account Security Solution gives security in numerous fields of an organization like password management, recording of the sessions.
It Give the security from the different threats to protect the session recordings and account credentials etc.
This CyberArk privileged account security is too used on cloud environment to protect from the threats and malware.
SSH keys management is very help to give the security in the account credentials from the unauthorized users.
There’s much more to tell you so let’s get to it with IdesTrainings, in Cyberark architecture explained in detailed by top real time trainers.
To essential threat diminish and to provide entire security of data assortment in many organizations also use McAfee. To be more familiar with privileged security solution join IdesTrainings, we also provide corporate McAfee Training.
We not only give CYBERARK training we also give CYBERARK project support if you have any doubts in your project. Our trainers will clear your doubts about CYBERARK project. Idestrainings is best for CYBERARK Job support. We have professional trainers for CYBERARK Job support. Our experts will explain about the CYBERARK benefits for your work/project. Idestrainings provides Best CYBERARK Job support by experts from India.
Why we need CyberArk Training?
- CyberArk privileged Account Security (PAS) solution is perform to create, secure, rotatae restriction access to privileged account passwords entire the enterprise IT region.
- The cyberark empower the enterprises to understand the opportunity of their privilege account dangers and focus controls in place to reduce those risks.
Empower the enterprises to accomplish harsh privileged access, automate workflows and change passwords at a regular interval without need of any manual IT attempt.
What are Privileged Accounts in CyberArk Training?
The privileged accounts are available in organization like windows machine having administration account and for UNIX machine there is root account etc.We are giving in detailed knowledge of privilaged accounts in CyberArk Online Training.
Every system to administrate and monitor that system it should require high privileged accounts such as administrator account. These privileged accounts can be like in best CyberArk Training:
- Elevated personal Accounts
- Shared Privileged Accounts
- App2APP Application Accounts.
Elevated personal Accounts: These are simply elevated personal accounts high privileged to perform many kind of activity in our network. You will learn CyberArk Training by the best trainers. CyberArk IAM Training is also available.
Shared Privileged Accounts: These shared privileged accounts are used by windows users or automated or scheduled task that is being used.
App2APP Application Accounts: One application uses one username and password to talk to another application or this application talk to database .These accounts are high privileged accounts. But every account having challenges with them.
- These accounts are used by every employee of an organization like IT Staff, System admin or Network Administrator or database administrator and also developers are use these accounts. These accounts are also used by application scripts, batch process, and Windows service in CyberArk Training.
- Every system should have one administrator account to administrate and monitor that system to perform any privileged operations on the system to get access the sensitive information of an organization.
- And these accounts are required in emergency or Disaster recovery and application to application communication or automated tasks and processes. More than 60+ students are trained in this CyberArk Training.
Who should attend the CyberArk Training?
- Identity and Access Management Professionals.
- Security Analysts.
- Security Administrators.
- Network Engineers.
- Security Operations Analysts.
Where CyberArk Privileged Account Security used?
CyberArk privileged account security is widely used in the many sectors like financial services, communication, and media, also in public sector also. In manufacturing department also we use CyberArk Training software. some of the industries are:
Financial services: (CyberArk training)
- In credit card information communication and clearance payment & services transactions between banks, credit cards we use Cyberark privileged security solution.
- To communicate with the internal branches of financial transactions. And transferring legal files and emails with VIP customers. Idestrainings provide CYBERARK Job support at reasonable price.
Insurance:
- CyberArk Training is widely used in claims processing of investigators data we use this CyberArk privileged account security. And data from benefits provider of claiming customers.
- Claim processing of the private investigators’ information also secured by the CyberArk.
Life Science and healthcare:
- In pharmaceutical departments we have to transfer information within the labs and researchers we use CyberArk Training software solutions.
- In healthcare department, severe injuries detailed information is secured by using this.
- Personal health data between hospitals and healthcare providers.
To provide the password identity management and how the information is accessed by the user from any system or from a cloud with securely by using SailPoint. To know in detail we provide SailPoint Training by real-time Trainers. CyberArk Training certification is also provided.
CyberArk privileged security solutions offerings: (CyberArk training)
Best CyberArk Online Training Privileged Account Security Solutions offerings can be categorized into 3 broadly categories.
- Shared Technology platform
- proactive controls
- Real-time threat detection
Shared Technology platform:
This is the foundation level. In this foundation level having the important secure digital vault. In this, we have 4 components are there. They are:
- Web Management Interface
- Master Policy
- Discovery Engine
- Secure Digital Vault
Web Management Interface: By using the web management interface we enter the secure digital vault. We use the centralized web management interface is used to implement policies and to do administrator task.
Discovery Engine: Using the discovery engine tool we can quickly on board in UNIX machine and windows machine.
Master Policy: This is in Granule level and we can enforce policies. This is one of the components of a shared technology platform in CyberArk Training.
Secure Digital Vault: CyberArk took this secure digital vault from the banking sector. CyberArk uses seven layers of security around the digital vault. This digital vault is very crucial all the credentials are stored in a digital vault.
The seven layers of security in best CyberArk Online Training are:
- Hierarchical Encryption
- Tamper-proof Audit ability
- Comprehensive Monitoring
- Segregation of Duties
- Firewall
- Authentication
- Session Encryption
Even you can check this:
We not only give trainings CYBERARK but also give CYBERARK project support if you have any doubts in your project. Our trainers will clear your doubts about CYBERARK project. Our experts will explain about the CYBERARK benefits for your work/project.
- The Cyber-Ark Secure Digital Vault
- Focal Policy Manager
- CPM and PVWA Installation
The PAS Web Services is a Restful API:
Version 10.6 of the CyberArk Privileged Access Security (PAS) Solution includes a feature that enables this option. The PAS Web Services SDK is a Restful API that can be invoked by any Restful client for various programming and scripting environments, including Java, C#, Perl, PHP, Python and Ruby.
- CyberArk’s Privileged Identity Management (PIM) Suite is deliberated and built-up by means of an extensible architecture come up to, which supplies great flexible to with passion added administer devices.
- CyberArk constantly releases CPM plug-ins for new platforms as part of and between official releases of the PIM Suite. Plug-ins is self-sufficient mechanism used by the CPM for communicating with definite appliance types.
- CyberArk carry out testing on particular appliance description, but supply clients an recognition Testing Procedure which allows them to use the product with older or newer versions of these devices, and enables CyberArk to support.
IdesTrainings Provide CyberArk related course like RSA Archer Training by the real-time trainers with good material and videos. We provide training for Individual or corporate batches also.
- The CyberArk PIMis well maintained, unmanaged privileged accounts to the security issues that can cause damage to the accounts and can lead to loss of money.
- Many organizations are leading to the cloud computing today. Whereas this is secure and improves their profits. To protect your data, to assure your data should follow the security methods, for the cloud and service providers, the Cyberark PIM will give the control.
- Through the single central interface, you can view the accounts, depending on the organizations there are shared and privileged accounts, some authentications gives you an assurance of the accounts then the process will be correct.
- In Cyberark PAS Trainingthere are some features of CyberArk, there can be attacks on the information like the cyber attackers, and Cyberark PAM will protect the information from these kinds of issues.
Proactive Controls:
CyberArk Training having these important components like:
Enterprise Password Vault (EPV): Cyberark EPV(Enterprise password vault) is a component of privileged account security solution and is described to create, secure, and Password Vault Web Access(PVWA) rotate and restrict the access to privileged account passwords used to access systems.
Privileged Session Manager (PSM): Cyberark PSM allows the enterprises to remove, monitor, history as well as restrict privileged period on diagnostics systems including Windows, DBs, network devices, UNIX. Complete traceability is done this PSM. The solution acts as a jump server and single access control point, avoid misalliance from activating to a particular system and maintain keystrokes and commands for continuous observation. It provides all recording of each session.
- Cyberark Privileged Identity Management is a secure policy-based solution, which will be securing and managing the privileged data in the Cyberark patented digital vault, here there will be trusted applications.
- The passwords are centralized and stored in the Cyberark patented digital vault, for the data security bridge the Cyberark privilege Identity management, you can even know that who is accessing your system, and also you can see the work they are doing.
- For example there are service providers those passwords are with the administrator then anyone can access your device it will become an issue, so with the Cyberark PIM and Cyberark IAMeverything is recorded and monitored and stored safely stored, there will be some policies to access your services here you can easily check that who has done the operations and details of it.
- These security policies are in the Central management only, the admin or the customers can access the accounts.
- Application Identity Manager (AIM): Cyberark AIM is the component of CyberArk. It deletes the fixed credentials from application code, configuration files and SSH keys from servers, building them unreachable to attackers and malicious insiders. We provide Corporate CyberArk AIM training with good material.
- And securely store and move these application passwords and SSH Keys automatically based on policy, without impacting the application performance or creating downtime.
- It also allows a request to credentials based on the path, OS user and more. And it allows only authorized applications can access mandatory credentials.
Central Policy Manager (CPM): CyberArk CPM manages the account passwords automation like reset password, forgot password, verify password these all are managed by this Central Policy Manager.
End Point Management (EPM): EPM is only for endpoints of an organization. Cyberark EPM solutions provide major things. One is least privileged management and credentials theft management. It also called as CyberArk viewfinity.
SSH Key Manager: This protects the accessing by malware by using the SSH Key. And it gives control power to access private keys. We provide the best Knowledge of Cyberark Training SSH key manager.
DNA: Discovery and Audit (DNA) is a pre-sales tool to determine the privileged attack top of the enterprises by identifying where privileged accounts available on-premises and in a cloud. And also identifies the account security risks, vulnerable to credential theft attacks.
On-Demand Privileged Manager: Cyberark Training On-Demand privileged manager is responsible to identify the account credentials information and define the permissible rules to access the account. It plays a vital role in the CyberArk privileged Account security Solutions.
Real-time threat detection:
Privileged threat analytics (PTA) is nothing but a security threat intelligence solution activity which is provided by the CyberArk. It generally works based on the risk score means each command or each activity that user did. It is responsible to identify the attacks done on privileged accounts.
To identify the exact threats accurately within the span of time and take action prior to the systems are affected and helps them to protect from unauthorized users by using ArcSight SIEM. We are providing best ArcSight Training by the Real-time trainers.
We explaining the cyberark training with covering all the related topics, and in this training we also give training about cyberark 10.1 online training.
Cloud Security by using Best CyberArk Online Training:
Cyberark privileged account security plays an important role in the cloud computing environment.
It having good capabilities to protect the credentials and session security and also provide security for maintenance.
CyberArk having tool called DNA. Using this tool we analysis the AWS assets.
CyberArk Training provides security and watching access to the AWS Management Console. It gives security to the credentials and for auto-scaling applications.
Automated deployment of the CyberArk Environment in AWS using Cloud Automation tool. You can learn all these basics in CyberArk training.
Let me know what is AWS..? AWS stand for Amazon Web Services; present days AWS is largest cloud computing platform and it is the popular terminology.
It is store the data in the cloud, from the devices connected to the cloud. Cloud computing is the paradigm shift that provides computer over the internet. Idestrainings has experts for CYBERARK job support; they will trained on your project/subject also in flexible hours.
A cloud computing services consists of highly optimized virtual data centers that provide, various hardware, software and information resources for use.
When needed organizations can simply connect to the cloud and use the available resources on pay per use basis.
Conclusion of CyberArk Training:
CyberArk is an information security company that provides network vault like technology to customers. It surrounds the sensitive data with layers of security within the existing network perimeter and can be deployed on the cloud, on-premises, and across OT/SCADA environments.
Idestrainings provide best CyberArk training by our highly skilled consultants. The reason for CyberArk training is to safely manage, store and turn special credentials, and give a way to clients to get to these credentials safely. CyberArk is software protects the high value resources of driving organizations and government associations around the globe. We also provide the classroom training at client premises Noida, Bangalore Gurgaon, Hyderabad, Mumbai, Delhi and Pune.

