
Identity and Access Management Training Introduction:
Identity and Access Management Training with IdesTrainings- Identity and access management is the most important aspect of information security, managing user identities and their access to enterprise resources and data. Programs, including IAM governance and policies, processes and technologies, maintain user identities and implement what they can and cannot access in the system through authentication, authorization, and accounting. Idestrainings is best in providing Identity and Access Management online training by real time experts from India at flexible timings. In this Identity and Access Management Training, you will get a virtual learning experience from basic level to advanced techniques. We provide both online and corporate training for Identity and Access Management Course. Join Today!
Prerequisites of Identity and Access Management course:
The people who are going to take the Identity and Access Management Training:
- Should have the basic knowledge on Java.
Identity and Access Management online training outline:
- Course Name: Identity and Access Management Online Training
- Mode of training:Online Training and Corporate Training (Classroom training at client location)
- Duration of course:30 hrs
- Do you provide materials:Yes, If you register for IAM online training with IdesTrainings, the materials will be provided.
- Course fee: After register with IdesTrainings, our coordinator will contact you.
- Trainer experience: 10 years+
- Timings:According to one’s feasibility
- Batch Type:Regular, weekends and fast track
- Sessions will be conducted through WEBEX, GoToMeeting OR SKYPE.
- Basic Requirements: Good Internet Speed, Headset.
IDENTITY AND ACCESS MANAGEMENT ONLINE TRAINING COURSE CONTENT
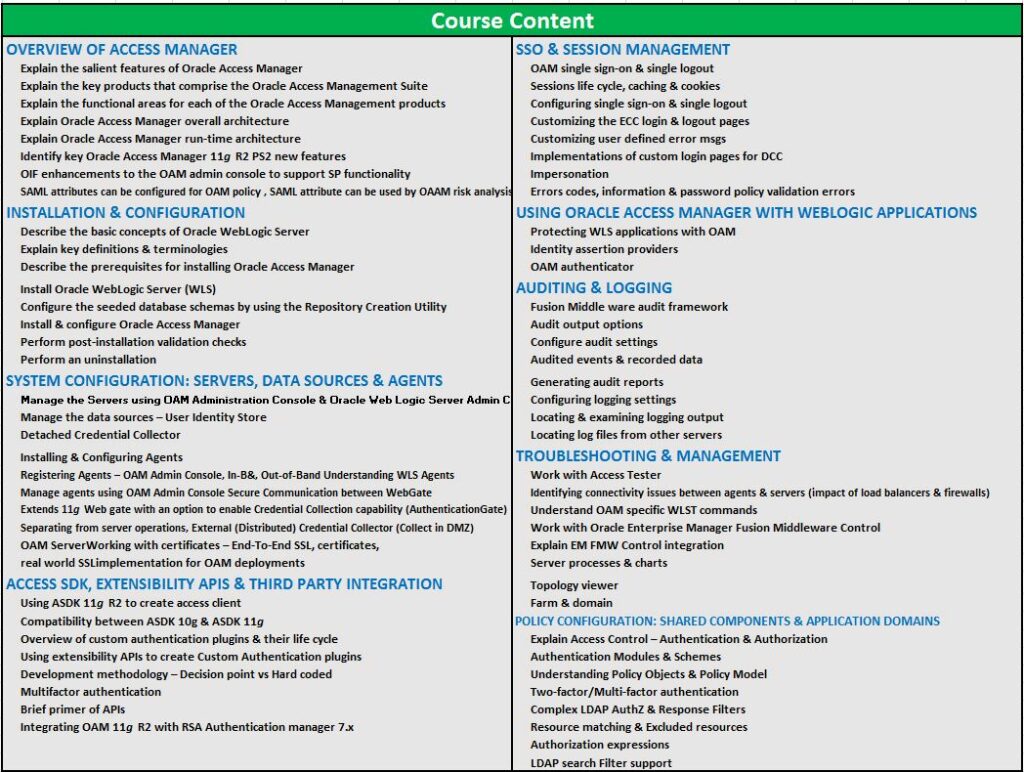
Overview of Identity and Access Management course:
Identity and access management is a combination of both software and database, which is used to create the management of individual identities. Most of these Identity Management functions are based on a strong foundation of consolidated personal data, which is used to create and manage privilege rights. When a personality has been built up for an individual, it very well may be overhauled on a progressing premise contingent upon the jobs the individual takes in the association. Different ID the executives frameworks and apparatuses empower the chairman to make a client ID, track it on a progressing premise, and make changes when required.
Implementation of IAM:
- List and evaluate the laudable investments and processes. Clean and consolidate identity data stores. Create virtual identities for enterprise users.
- Design and implement identity infrastructure components. Create identity provisioning and enforce password management, user self-service and control compliance.
- Deliver applications and services. Access management has been implemented to a clean environment. Utilize federal recognition to improve the supply chain and employee capabilities.
What is Identity and Access Management?
Identity and Access Management is the security discipline that enables the right individuals to access the right resources at the right time for the right reasons, here we need to manage the life cycle of the users we need to make sure the user claims to be access of our users management and it must be hard to gain the access must fulfil the security policies.
The Components that build a typical enterprise Identity and Access Management solution:
Corporate Directory
- LDAP or Active Directory
Most of the companies are invested in the some single sign-on or SSO capabilities these were often focusing on internal applications and used as non-standard methods of achieving single Sign-on but once the company started to interact with more number of external parties such as partners and software as a service.
Web SSO
- Internal applications
- Web Access Management
SaaS applications federation was needed these solutions very much are built on the standards and you can integrate products from many different vendors because of that closely tied to SSO.
Federated SSO
- External Application
- Cloud Applications
- Standards based
Multi-factor Authentication
Federation are the need for multi-factor authentication or MFA with the use, the multi-factor authentication will have the higher trust level.
Automates Provisioning
- Directory or HRMS Driven
- Request & Approval Workflow
- Provision to on-prem and SaaS apps
The user with an ever-growing catalog of application directories partners of SaaS application, we need something that can help with the lifecycle of the users.
Compliance/Identity Governance
- Segregation of Duty
- Attestation/Access Certification
- Audit& Analytics
The Capabilities to monitor and audit our identity and access management solution to make sure the right person has the right access at the right time and for the right reasons. IdesTrainings provide the online and corporate training for Identity access management and we also job support for identity access management training and also we provide training for IBM Tivoli identity management training.
Who can go for Identity and Access Management course?
An early or intermediate level of identity and access management and works for various government agencies, businesses and technology companies around the world to design, implement, improve or maintain identity and access management programs, processes and tools.
How does the IAM works?
This process involves creating user accounts that can be edited, disabled or deleted. Representative workflows, rules and procedures apply to the user’s account.
A user profile will tell the company: who they are, what they are entitled to do, when they are allowed to perform specific functions, where they are allowed to perform functions from and why they have been granted permissions.
Benefits of Identity and Access and Management service:
By implementing access control and identity management solution, a company can gain the following benefits:
- Proper identity management gives companies greater control of user access and reduces the risk of a data breach.
- Access is provided based on a single description of an existing policy.
- IAM also strengthens internal policy compliance and reduces the financial, labour and time resources required for this end.
- Automated IAM frameworks increment worker efficiency by diminishing the exertion, time and cash required to physically perform IAM undertakings.
- IAM helps organizations comply with government regulations as they receive the necessary action and provide on-demand reports for audit.
Conclusion to Identity and Access Management Training:
Identity and Access Management Training includes a system of processes, procedures, and technologies used to create, store, and manage user identities and permissions. The use of IAM solutions ensures strong data security, access management, internal and external policy compliance. It can increase employee productivity, reduce IT overhead costs and reduce the risks of data breaches.
This Identity and Access Management program is produced by IdesTrainings team of professionals who have built IdesTrainings. We have great hands-on learning and practical experience for IAM Training. IdesTrainings Classroom provides the best Identity and Access Management Online Training also. We are providing best in the online mode for IAM Training and we are providing the video tutorials and job support for Identity and Access Management. We also provide the classroom training of Identity and Access Management Training at client permission in Noida, Bangalore, Gurgaon, Hyderabad, Mumbai, Delhi, and Pune.

