
Introduction to PKI Training:
PKI Training- PKI stands for Public Key Infrastructure. To get the underlying security services, Public Key Infrastructure uses a pair of keys. PKI Training is offered by IdesTrainings. It is one of the best online training providers in India. Our training system is designed in such a way that students are able to learn their interested technology from anywhere in the globe at their convenient time. Our trainers have more than 10 years of experience in their respective field. We provide the best interactive and informative PKI online training. Classes are available for the individual as well as for corporate batches on demand.
All our students are very satisfied with our online training. The classes are taken here in flexible-hour, participants can take their classes at their spare time as per personal schedule.
Prerequisites for PKI Training:
To learn PKI Training at our IdesTrainings that candidate should have a basic knowledge on
- Windows Servers and Networking
This course is useful for Active Directory Certificate Services.
PKI Online Training Course Details:
- Program Name:PKI Training/PKI Corporate Training/PKI Online virtual classes.
- Course Duration:35 Hours.
- Mode:Online virtual classes and corporate.
- Timings:According to one’s feasibility.
- Trainer Experience:10+ years.
- System Access:will be provided.
- Batch Type:Regular, weekends and fast track.
- Trainees will get the soft copy material.
- Sessions will be conducted through WEBEX, GoToMeeting OR SKYPE.
- Basic Requirements: Good Internet Speed, Headset.
PKI ONLINE TRAINING COURSE CONTENT
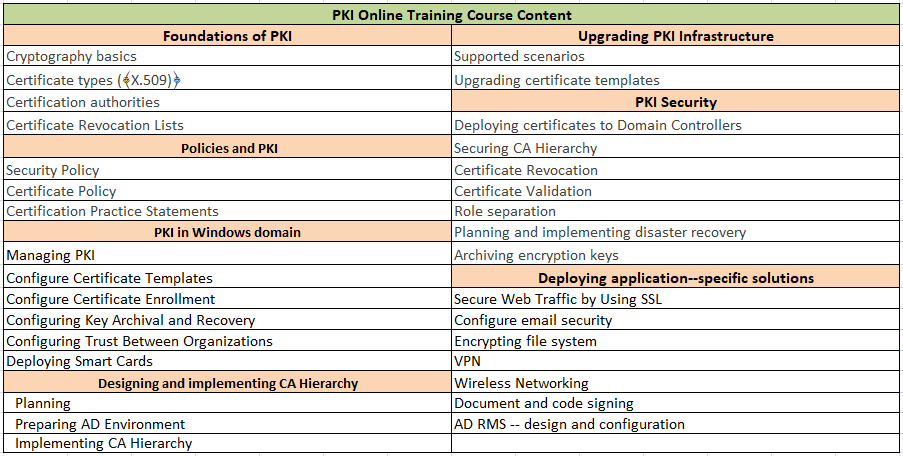
Overview of PKI training:
Learn about Public Key Encryption or Asymmetric Key Encryption in our Public Key Infrastructure Corporate Training:
Let’s have a look at what exactly the public key encryption is. We have two different keys for encrypting and decrypting the data in the public key encryption. There is a mathematical relation between these two keys. They are private key and public key. Public key is always public to everyone while private key belongs to those who create these two ways. In order to prove the sender, we need technique called digital signature. This is a brief introduction of public key encryption. We will be covering all these basic topics of public key infrastructure in our PKI online training.
“IdesTrainings Team will be in switch on mode for 24/7 and will solve any issues regarding the training, timings, trainer or server.”
What is meant by PKI Training?
In this course we’ll discuss PKI which implies Public Key Infrastructure. This course furnishes understudies with the information and abilities to convey and deal with a 2-level open key foundation (PKI) on windows servers to help applications that require endorsement based security. Understudies get hands-on experience executing the answer for secure sites, applications and gadgets.
What you will learn in this PKI Training:
- Create and deal with a venture wide Public Key Infrastructure (PKI).
- Identify usefulness of PKI segments.
- Manage the issuance and repudiation of computerized authentications.
- Integrate computerized endorsements into a scope of utilizations.
- Install, Configure and Manage 2-level PKI chain of command on Windows Server 2012 R2.
- Will have inside and out comprehension of designing accreditation benefits on Microsoft condition.
- How SSL are utilized to Secure site utilizing authentications.
- How independent machines or gadgets demand declarations utilizing NDES, CEP/CES.
- Configure CDP/CIA expansions, OCSP server.
- Understand how encryption/unscrambling cooperates.
- How to Migrate Hashing Algorithm from SHA1 to SHA2 (SHA256) on two level PKI order.
For Whom this PKI Training is?
- This Course is intended for crowd of different kinds from tenderfoot to master, so no earlier information on PKI is required.
- Students who are functioning as an IT expert and need to find out about Active index Certificate Services a.k.a ADCS on Windows Infra.
- Students who are in Cyber security or Identity and Access Management space.
Why you can take this PKI Training?
There are numerous motivations to take this course.
This course is structured by Microsoft Official Curriculum and educated by Microsoft Certified Trainer.
- Knowing the understanding level of understudies whether they are amateur or propelled, this course is intended for all levels making it best fit for everybody.
- You’ll discover loads of Hands-On in this course which will make you for all intents and purposes sound.
- And progressively over security is a hot subject in the present advanced age, so why not find out around one of the major and most well known procedure to verify your IT Infrastructure.
- At last, I am anxious to see you succeed, I am offering you my assistance, help any place required in learning this course. You can drop your inquiries in the Q&A segment of the course and I’ll ensure it will be reacted immediately.
Learn about Digital Signature in our PKI training:
Digital signature is almost equals to a hand writing signature. It is nothing but an electronic verification of the sender. There are three main duties of digital signature. Let’s have a look at each of them. The first purpose is authentication. A computerized mark gives the recipient motivation to trust the message was made and sent by the guaranteed sender. There is another purpose called non-repudiation. With the help of the digital signature, the sender can’t deny having sent the message later on. Next one is integrity. The digital signature guarantees that the message was not adjust in travel. These are basically used for financial transactions, and also software distribution. There are most popular with email users. This is just a brief introduction of digital signature. We will be covering these topics in our Public Key Infrastructure Corporate Training.
Learn basics of PKI in our PKI training:
- PKI stands for Public Key Infrastructure. Public Key Infrastructure is nothing but a two key asymmetric crypto system.
- Public Key Infrastructure is actually a framework that empowers IT industry to maintain high level of confidentiality via data encryption.
- Public Key Infrastructure is a framework for managing the public key encryptions and digital certificates. The main purpose of the Public Key Infrastructure is to provide the secure transformation of the information over the internet.
- There are so many procedures, standards, and policies in the Public Key Infrastructure. Here we are interacting with strangers over the internet.
- Then there is a trust conflict comes into picture. In the Public Key Infrastructure, actually trust comes from the third party i.e. Certificate Authority (CA).
- Certificate authority is nothing but an entity that actually responsible for providing the digital certificates. Certificate authority is actually external to the company and they actually charge for the service for example Global sign.
- Certificate authority is also internal to company. This is a brief introduction of Public Key Infrastructure. We will be covering all these topics in our PKI training.
“We provide training by our well experienced trainers.”
Learn about Public Key Infrastructure hierarchy in our PKI training:
- We need to understand how the certificate hierarchy works in order to implement a good hierarchy.
- We have mainly three different hierarchies available in PKI. You can actually choose you hierarchy that will meet your needs.
- First of all, you have to choose the size of the company and the next one is geographic distribution of the company. The certificates have to be verifying online before we use.
- The types of Public Key Infrastructure are single-tier hierarchy, two-tier hierarchy, and three-tier hierarchy.
- Single-tier architecture is nothing but a network that contains only one certificate authority. This type of hierarchy is widely used in the small organizations. This does actually cause for security concern.
- There is no redundancy and it has less administration. Let’s have a look at two tier architecture. The two-tier architecture provides functionalities or redundancy.
- You can add many more certificate authorities. The next hierarchy is three-tier architecture. This type of hierarchies give more security for Certificate authority infrastructure when compare with the previous hierarchies.
- Three-tier hierarchy is also more flexible when we compare with other hierarchies. There is no need to be available in online for internal and external CA.
- Once you choose what hierarchy you would like to deploy in your organization, the next that you have to focus is the validation of certificate.
- This is just a brief introduction of different hierarchies. We will be discussing all these concepts in our Public Key Infrastructure online training.
Learn Microsoft Azure Training along with PKI Training:
Microsoft Azure is related to cloud computing services and it is one of the most popular Clouding Services. This is used to develop and to maintain the applications. Microsoft Azure provides Software as a Service (SaaS), Platform as a Service (PaaS) and Infrastructure as a Service (IaaS). The programming languages are also supported by Microsoft Azure.
Benefits of Microsoft Azure Training:
Some of the benefits of Microsoft Azure Training are as follows.
- This is used to develop and also to maintain the apps in an easy way.
- We can also create a website.
- There is also a flexibility to pay for what we have consumed.
- Azure is the most updated technology with the infrastructure and its applications.
These are just the basics of Azure Training and you in detail about Azure Training along with PKI Training.
Along with PKI Training learn Microsoft Access Training:
Microsoft Access is one of the tools that are related to data management. This tool is used to save the data for analysis. It stores the data in Access Jet Database Engine. Here we can also transfer the data.
Features of Microsoft Access Training:
Some of the features of Microsoft Access are as follows.
- It is more flexible for individual users and also for small teams.
- It can be easily understood when compared with client-server database.
- We can easily transfer to other Microsoft office and also to applications.
- There are templates for creating and publishing the data.
These are some of the important points of Microsoft Access Training and you will get the detail knowledge on Microsoft Access Training along with PKI Training.
Objectives of PKI Training:
Toward the finish of the course you will have the option to:
- Learn how to assess and choose proper PKI innovation
- Understand the advantages of testaments utilized in the foundation
- Learn how to introduce and arrange PKI condition as indicated by the accepted procedures taken from useful experience
- Learn how to pick the correct design, framework, and practices for PKI execution
- Learn how to deal with the declaration lifecycle
- Adjust PKI to your business needs
- Become acquainted with cutting edge PKI settings and executions
Conclusion to PKI Training:
PKI Training is one of the most demanding course in the present market. Many organizations are looking for the candidates who are having good practical knowledge on PKI course. They are ready to pay huge salaries. This is the Wright time to learn PKI Training. IdesTrainings is the best for Public Key Infrastructure online training. We are the best online training providers;
“Then why are you waiting for….? join with us”
We just don’t teach you the technologies rather we make you understand with live examples, the sessions we conduct are interactive and informative. If the candidates miss any of the sessions due to some unavailability, we will give assurance for backup sessions. There is a huge demand for PKI professionals. There is a good salary for PKI professionals. We are ready to solve any issues within no time. We are providing the best online PKI training at a reasonable price. We have core team of experts for this PKI training. As it is an online training, the training timings will be the candidate feasibility. For details of this PKI online training course, you can contact with the Idestrainings team.

